Today, I visited one of those ad-laden but otherwise legitimate
sites with lots of top 10 lists. In this case, it was a list of
photos which looked too cool to be real. I got there from a link
chain starting at a Lego article on Epic Win which had a link to
the original photo which then had a link to similar stuff etc. It
was a long chain of sites I normally wouldn't visit, but which were
legit and interesting, if not ad-laden. No, no porn :)
Anyway, as I clicked on a link for another story, bam! Security
essentials popped up in the corner and at the same time, I got 5
UAC "do you want to allow this program to make changes to your
computer" warning dialogs (one after the other). I answered "no" to
all of them, of course.
I haven't had a computer virus or trojan on my own machines
since around 1992 at work when I got a DOS boot sector virus off a
5 1/4 floppy that was stored in a decade-old Compaq (or Kaypro?)
luggable we pulled out of storage to allow another data entry
person to do some work. Yeah, that was a pretty vintage virus, even
then.
To repeat: I have not had a virus or trojan on any of my PCs at
home or work since 1992, and I've never had a virus or trojan on a
machine personally owned by me. Ever.
Here's the info from Microsoft Security Essentials.
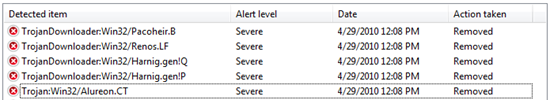
I run as an admin on my Windows 7 machine, so UAC was definitely
a saving feature. As I understand it, that first trojan went and
downloaded all the other downloaders, and then attempted (but
failed due to UAC) to modify DNS on my machine. The trojan itself
was downloaded to:
C:\Users\Peter.Brown\AppData\Local\Temp\acesrnomwx.exe
After the trojan and the downloaders were removed, I had to do
an ipconfig/renew to get DNS back. I think Security Essentials did
some stuff to DNS just in case.
Moral of the Story
Risky sites (like porn sites and whatnot) are still one of the
largest vectors of viruses (besides links in email and facebook), so
you do well to avoid them. However, even seemingly legit sites can
have trojans on them. Safe surfing is not enough to protect you
from drive-bys on sites with either infected ads or hijacked
pages.
Leave UAC on in Windows 7. It's pretty transparent, and a better
implementation than we had in Vista. Then make sure you have
anti-virus software running. With free products like Security Essentials, there's no excuse.
